Generate Gpg Key Command Line
11.12.2020 admin
Using the gpg -edit-key UID command for the key that needs to be signed you can sign it with the sign command. You should only sign a key as being authentic when you are ABSOLUTELY SURE that the key is really authentic!!! So if you are positive you got the key yourself (like on a key signing party) or you got the key through other means. The Red Hat Customer Portal delivers the knowledge. Creating GPG Keys Using the Command Line. This command generates a key pair that consists of a public and a private key. Other people use your public key to authenticate and/or decrypt your communications. Distribute your public key as widely as possible, especially to people.
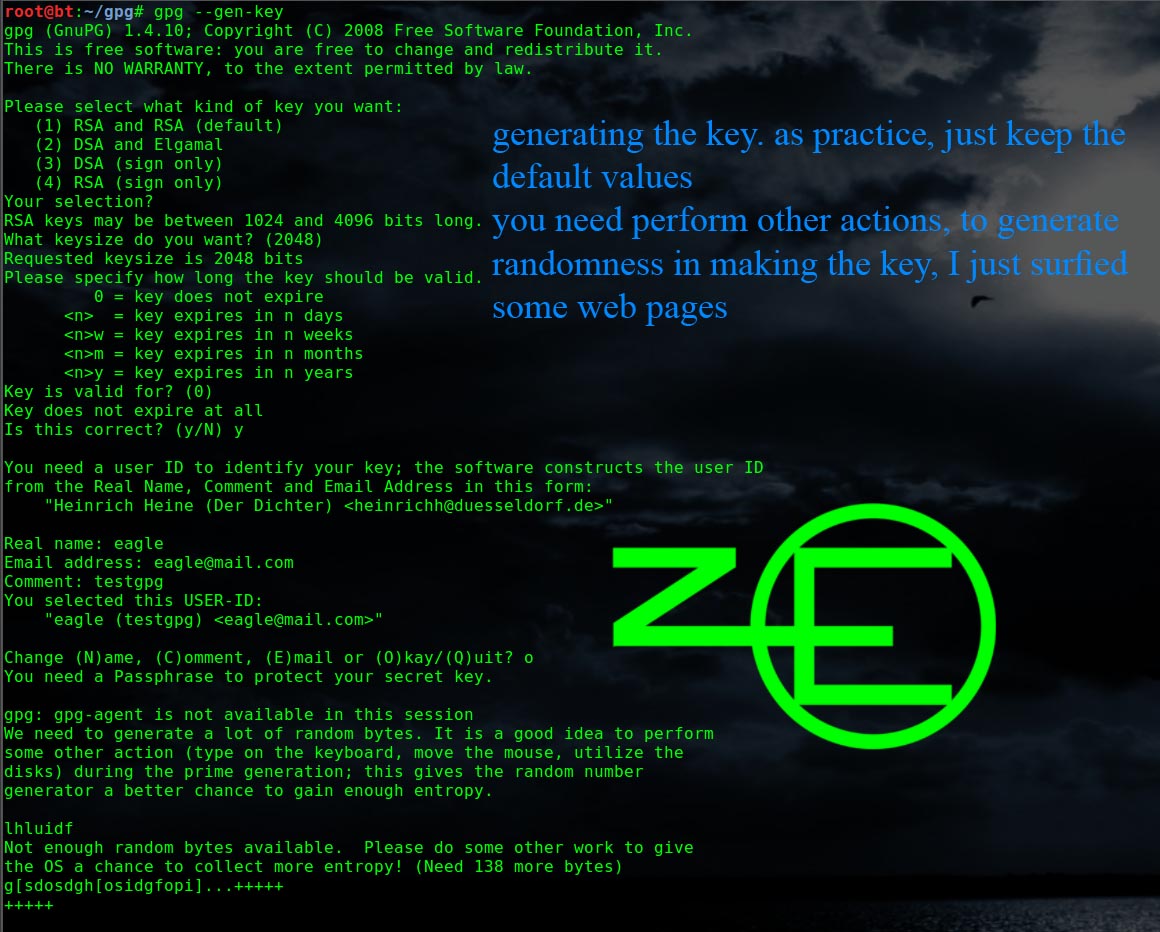
- How to work with PGP keys using GnuPG. To generate your key pair, we'll work from the command line. Open a terminal window and issue the following command: gpg -gen-key.
- May 26, 2017 You can import someone’s public key in a variety of ways. If you’ve obtained a public key from someone in a text file, GPG can import it with the following command: gpg -import nameofpubkeyfile; There is also the possibility that the person you are wishing to communicate with has uploaded their key to a public key server.
- Generating a Keypair. To begin using GnuPG, you must first generate a new keypair: a public key and a private key. To generate a keypair, at a shell prompt, type the following command. To trust your key, type the following command (replace ): gpg -edit-key At the Command prompt type trust and select 5 = I trust.
- The command expects the files to bee verified either on the commandline or reads the filenames from stdin; each anem muts be on separate line. The command is intended for quick checking of many files.list-keys names, -list-public-keys names List all keys from the public keyrings, or just the ones given on the command line.
Generate Gpg Key Command Line Code
Encryption/decryption commands
- To encrypt a plaintext file with the recipient's public key:
- To sign a plaintext file with your secret key:
- To sign a plaintext file with your secret key and have the outputreadable to people without running GPG first:
- To sign a plaintext file with your secret key, and then encrypt itwith the recipient's public key:
- To decrypt an encrypted file, or to check the signature integrityof a signed file:
Key management commands
- To generate your own unique public/secret key pair:
- To add a public or secret key file's contents to your public orsecret key ring:
- To extract (copy) a key from your public or secret key ring:
Update auto generated primary key sql server set identity_insert. or
- To view the contents of your public key ring:
- To view the 'fingerprint' of a public key, to help verify it overthe telephone with its owner:
- To view the contents and check the certifying signatures of yourpublic key ring:
- To edit a key:
- To remove a key or just a userid from your public key ring:
- To permanently revoke your own key, issuing a key compromise certificate:
- To disable or re-enable a public key on your own public key ring:
or
Esoteric commands
- To create a signature certificate that is detached from the document:
- To detach a signature certificate from a signed message
Gpg Command Line Tool
Command options that can be used in combination with other command options
Generate Gpg Key
- To produce a ciphertext file in ASCII format, just add the -aoption when encrypting or signing a message or extracting a key:
- To specify a recipient, add the -r option followed by a user id:
- To specify an output file, add the -o option followed by a filename: