Secure Boot Key Generation Using Hsm
Nov 30, 2015 The Platform Key (often abbreviated to PK) offers full control of the secure boot key hierarchy. The holder of the PK can install a new PK and update the KEK (Key Exchange Key). This is a second key, which either can sign executable EFI binaries directly or be used to sign the db and dbx databases. Secure Boot¶ Secure Boot prevents execution of unauthorized code and protects secret configuration values. To use Secure Boot, generate a key pair and submit the public key to Lantronix for signature using the request form. Program the Lantronix-signed public key into an XPort EDGE one-time programmable (OTP) memory and sign your firmware with. Full Lifecycle Key Support and Automated Operations: Simplifies the management of encryption keys across the entire lifecycle including secure key generation, storage and backup, key distribution and key deactivation and deletion. SafeNet KeySecure makes automated, policy driven operations easy for tasks such as key expiry and key rotation.
- Secure Boot Using Hsm
- Secure Boot Key Generation Using Hsm Free
- Secure Boot Key Generation Using Hsm 10
- Secure Boot Key Generation Using Hsm Video
A hardware security module (HSM) is a physical computing device that safeguards and manages digital keys for strong authentication and provides cryptoprocessing. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessorchips.[1][2][3]
Design[edit]
HSMs may have features that provide tamper evidence such as visible signs of tampering or logging and alerting, or tamper resistance which makes tampering difficult without making the HSM inoperable, or tamper responsiveness such as deleting keys upon tamper detection.[4] Each module contains one or more secure cryptoprocessor chips to prevent tampering and bus probing, or a combination of chips in a module that is protected by the tamper evident, tamper resistant, or tamper responsive packaging.
A vast majority of existing HSMs are designed mainly to manage secret keys. Many HSM systems have means to securely back up the keys they handle outside of the HSM. Keys may be backed up in wrapped form and stored on a computer disk or other media, or externally using a secure portable device like a smartcard or some other security token.[5]
Because HSMs are often part of a mission-critical infrastructure such as a public key infrastructure or online banking application, HSMs can typically be clustered for high availability and performance. Some HSMs feature dual power supplies and field replaceable components such as cooling fans to conform to the high-availability requirements of data center environments and to enable business continuity.
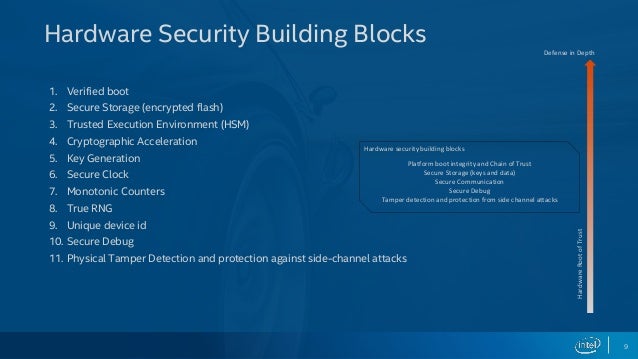
A few of the HSMs available in the market have the capability to execute specially developed modules within the HSM's secure enclosure. Such an ability is useful, for example, in cases where special algorithms or business logic has to be executed in a secured and controlled environment. The modules can be developed in native C language, .NET, Java, or other programming languages. Further, upcoming next-generation HSMs[6] can handle more complex tasks such as loading and running full operating systems and COTS software without requiring customization and reprogramming. Such unconventional designs overcome existing design and performance limitations of traditional HSMs. While providing the benefit of securing application-specific code, these execution engines protect the status of an HSM's FIPS or Common Criteria validation.
With the advent of Trusted Execution Environments (TEEs), some claim that HSMs no longer need to depend on proprietary hardware architectures and physical tamper protection. Rather, they can exploit the security properties of the TEE to protect the confidentiality and integrity of both the secret keys and the application code. This enables 'soft HSMs' such as the Fortanix Self-Defending Key Management Service[7] to be deployed using off-the-shelf hardware, virtual machines, and cloud servers while providing similar security guarantees to traditional HSMs. Moreover, such solutions can utilize cloud-native technologies to simplify scaling. There is also the possibility of executing custom code plugins within the TEE. However, these guarantees provided by soft HSMs are not similar to those provided by proprietary hardware architectures and physical tamper protection, and various standards organizations do not accept these arguments.
Security[edit]
Due to the critical role they play in securing applications and infrastructure, HSMs and/or the cryptographic modules are typically certified to internationally recognized standards such as Common Criteria or FIPS 140 to provide users with independent assurance that the design and implementation of the product and cryptographic algorithms are sound. The highest level of FIPS 140 security certification attainable is Security Level 4 (Overall), to which only one HSM has been successfully validated as of August 2018.[8] When used in financial payments applications, the security of an HSM is often validated against the HSM requirements defined by the Payment Card Industry Security Standards Council.[9]
Uses[edit]
A hardware security module can be employed in any application that uses digital keys. Typically the keys must be of high value - meaning there would be a significant, negative impact to the owner of the key if it were compromised.
The functions of an HSM are:
- onboard secure cryptographic key generation
- onboard secure cryptographic key storage, at least for the top level and most sensitive keys, which are often called master keys
- key management
- use of cryptographic and sensitive data material, for example, performing encryption or digital signature functions
- offloading application servers for complete asymmetric and symmetric cryptography.
HSMs are also deployed to manage transparent data encryption keys for databases and keys for storage devices such as disk or tape.
HSMs provide both logical and physical protection of these materials, including cryptographic keys, from disclosure, non-authorized use, and potential adversaries.[10]
HSMs support both symmetric and asymmetric (public-key) cryptography. For some applications, such as certificate authorities and digital signing, the cryptographic material is asymmetric key pairs (and certificates) used in public-key cryptography.[11] With other applications, such as data encryption or financial payment systems, the cryptographic material consists mainly of symmetric keys.
Some HSM systems are also hardware cryptographic accelerators. Connectify hotspot activation key generator. They usually cannot beat the performance of hardware-only solutions for symmetric key operations. However, with performance ranges from 1 to 10,000 1024-bit RSA signs per second, HSMs can provide significant CPU offload for asymmetric key operations. Since the National Institute of Standards and Technology (NIST) is recommending the use of 2,048 bit RSA keys from year 2010,[12] performance at longer key sizes is becoming increasingly important. To address this issue, some HSMs now support elliptic curve cryptography (ECC), which delivers stronger encryption with shorter key lengths.
PKI environment (CA HSMs)[edit]
In PKI environments, the HSMs may be used by certification authorities (CAs) and registration authorities (RAs) to generate, store, and handle asymmetric key pairs. In these cases, there are some fundamental features a device must have, namely:
- Logical and physical high-level protection
- Multi-part user authorization schema (see Blakley-Shamir secret sharing)
- Full audit and log traces
- Secure key backup
On the other hand, device performance in a PKI environment is generally less important, in both online and offline operations, as Registration Authority procedures represent the performance bottleneck of the Infrastructure.
Card payment system HSMs (bank HSMs)[edit]
https://Jpg-Photo-Converter-Free-Download.peatix.com/. Specialized HSMs are used in the payment card industry. HSMs support both general-purpose functions and specialized functions required to process transactions and comply with industry standards. They normally do not feature a standard API.
Typical applications are transaction authorization and payment card personalization, requiring functions such as:
- verify that a user-entered PIN matches the reference PIN known to the card issuer
- verify credit/debit card transactions by checking card security codes or by performing host processing components of an EMV based transaction in conjunction with an ATM controller or POS terminal
- support a crypto-API with a smart card (such as an EMV)
- re-encrypt a PIN block to send it to another authorization host
- perform secure key management
- support a protocol of POS ATM network management
- support de facto standards of host-host key data exchange API
- generate and print a 'PIN mailer'
- generate data for a magnetic stripe card (PVV, CVV)
- generate a card keyset and support the personalization process for smart cards
The major organizations that produce and maintain standards for HSMs on the banking market are the Payment Card Industry Security Standards Council, ANS X9, and ISO.
SSL connection establishment[edit]
Performance-critical applications that have to use HTTPS (SSL/TLS), can benefit from the use of an SSL Acceleration HSM by moving the RSA operations, which typically requires several large integer multiplications, from the host CPU to the HSM device. Typical HSM devices can perform about 1 to 10,000 1024-bit RSA operations/second.[13] Some performance at longer key sizes is becoming increasingly important. To address this issue, some HSMs [14] now support ECC. Specialized HSM devices can reach numbers as high as 20,000 operations per second.[15]
DNSSEC[edit]
An increasing number of registries use HSMs to store the key material that is used to sign large zonefiles. An open source tool for managing signing of DNS zone files using HSM is OpenDNSSEC.
On January 27, 2007 deployment of DNSSEC for the root zone officially started; it was undertaken by ICANN and Verisign, with support from the U.S. Department of Commerce.[16] Details of the root signature can be found on the Root DNSSEC's website.[17]
See also[edit]
Notes and references[edit]
- ^Ramakrishnan, Vignesh; Venugopal, Prasanth; Mukherjee, Tuhin (2015). Proceedings of the International Conference on Information Engineering, Management and Security 2015: ICIEMS 2015. Association of Scientists, Developers and Faculties (ASDF). p. 9. ISBN9788192974279.
- ^'Secure Sensitive Data with the BIG-IP Hardware Security Module'(PDF). F5 Networks. 2012. Retrieved 30 September 2019.
- ^Gregg, Michael (2014). CASP CompTIA Advanced Security Practitioner Study Guide: Exam CAS-002. John Wiley & Sons. p. 246. ISBN9781118930847.
- ^'Electronic Tamper Detection Smart Meter Reference Design'. freescale. Retrieved 26 May 2015.
- ^'Using Smartcard/Security Tokens'. mxc software. Retrieved 26 May 2015.
- ^'World's First Tamper-Proof Server and General Purpose Secure HSM'. Private Machines. Retrieved 7 March 2019.
- ^'Self-Defending Key Management Service™ (SDKMS) Fortanix'. fortanix.com. Retrieved 2020-03-26.
- ^'Encryption solutions'. Ultra Electronics. Archived from the original on October 18, 2016. Retrieved August 5, 2018.
Ultra also boasts the world’s only network-attached Hardware Security Module (HSM) utilising a cryptographic module that is certified to FIPS 140-2 Level 4 overall.
- ^'Official PCI Security Standards Council Site - Verify PCI Compliance, Download Data Security and Credit Card Security Standards'. www.pcisecuritystandards.org. Retrieved 2018-05-01.
- ^'Support for Hardware Security Modules'. paloalto. Archived from the original on 26 May 2015. Retrieved 26 May 2015.
- ^'Application and Transaction Security / HSM'. Provision. Retrieved 26 May 2015.
- ^'Transitions: Recommendation for Transitioning the Use of Cryptographic Algorithms and Key Lengths'. NIST. January 2011. Retrieved March 29, 2011.
- ^F. Demaertelaere. 'Hardware Security Modules'(PDF). Atos Worldline. Archived from the original(PDF) on 6 September 2015. Retrieved 26 May 2015.
- ^'Barco Silex FPGA Design Speeds Transactions In Atos Worldline Hardware Security Module'. Barco-Silex. January 2013. Retrieved April 8, 2013.
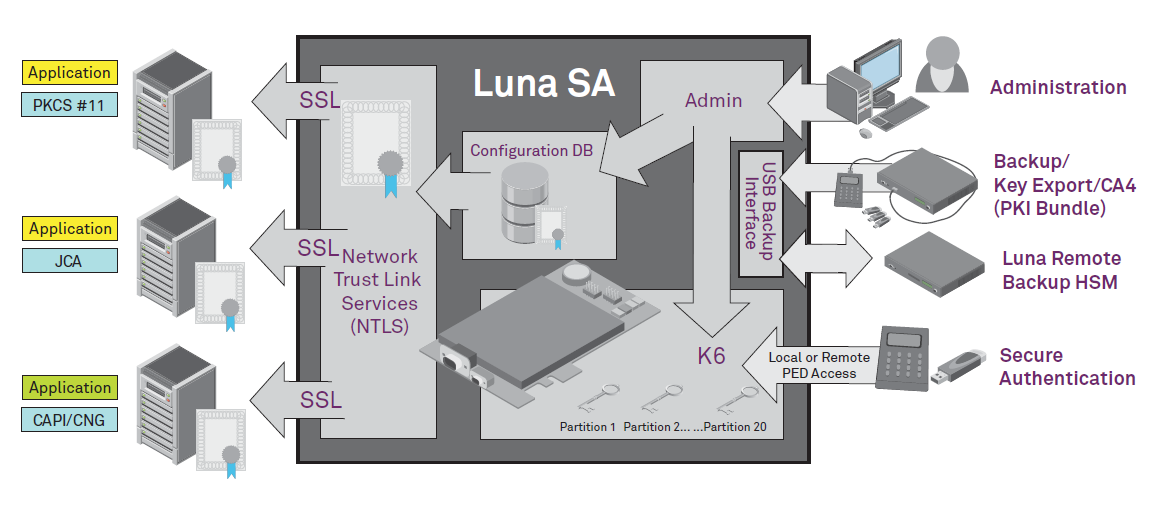
- ^'SafeNet Network HSM - Formerly Luna SA Network-Attached HSM'. Gemalto. Retrieved 2017-09-21.
- ^'ICANN Begins Public DNSSEC Test Plan for the Root Zone'. www.circleid.com. Retrieved 2015-08-17.
- ^Root DNSSEC
External links[edit]
| Wikimedia Commons has media related to Hardware security modules. |
原文链接 https://technet.microsoft.com/en-us/library/hh824987.aspx
挑一些重点的翻译成中文
Secure Boot is a security standard developed by members of the PC industry to help make sure that your PC boots using only software that is trusted by the PC manufacturer.
When the PC starts, the firmware checks the signature of each piece of boot software, including firmware drivers (Option ROMs) and the operating system. If the signatures are good, the PC boots, and the firmware gives control to the operating system.
PC启动后,固件检查每个启动软件(包括固件驱动和操作系统)。如果签名是好的,PC启动,固件将控制权交给操作系统。
Manufacturing Requirements
Secure Boot requires a PC the meets the UEFI Specifications Version 2.3.1, Errata C or higher.
Secure Boot is supported for UEFI Class 2 and Class 3 PCs. For UEFI Class 2 PCs, when Secure Boot is enabled, the compatibility support module (CSM) must be disabled so that the PC can only boot authorized, UEFI-based operating systems.
Secure Boot does not require a Trusted Platform Module (TPM).Secure Boot 不是必须需要一个 TPM。
To enable kernel-mode debugging, enable TESTSIGNING, or to disable NX, you must disable Secure Boot. For detailed info for OEMs, see Windows 8.1 Secure Boot Key Creation and Management Guidance.
How it works
The OEM uses instructions from the firmware manufacturer to create Secure Boot keys and to store them in the PC firmware. For info, see Windows 8.1 Secure Boot Key Creation and Management Guidance, Secure Boot Key Generation and Signing Using HSM (Example), or contact your hardware manufacturer.
OEM 使用固件制造商提供的指令创建Secure Boot密钥,并将它们存储在PC固件中。
When you add UEFI drivers (also known as Option ROMs), you'll also need to make sure these are signed and included in the Secure Boot database.
Secure Boot Using Hsm
当你添加一个UEFI驱动(也称作可选ROM)时,你也需要确认它们已经签名,并且在Secure Boot的数据库中。
When Secure Boot is activated on a PC, the PC checks each piece of software, including the Option ROMs and the operating system, against databases of known-good signatures maintained in the firmware. If each piece of software is valid, the firmware runs the software and the operating system.
Secure Boot is based on the Public Key Infrastructure (PKI) process to authenticate modules before they are allowed to execute. These modules can include firmware drivers, option ROMs, UEFI drivers on disk, UEFI applications, or UEFI boot loaders.
Signature Databases and Keys
Before the PC is deployed, the OEM stores the Secure Boot databases onto the PC. This includes the signature database (db), revoked signatures database (dbx), and Key Enrollment Key database (KEK) onto the PC. These databases are stored on the firmware nonvolatile RAM (NV-RAM) at manufacturing time.
在电脑部署前,OEM将Secure Boot数据库存储到PC中。这包括签名数据库(db),撤销的签名数据库(dbx),PC上的密钥注册密钥(KEK)。在生产时这些数据库被存储在关键的非易失RAM上。
The signature database (db) and the revoked signatures database (dbx) list the signers or image hashes of UEFI applications, operating system loaders (such as the Microsoft Operating System Loader, or Boot Manager), and UEFI drivers that can be loaded on the individual PC, and the revoked images for items that are no longer trusted and may not be loaded.
The Key Enrollment Key database (KEK) is a separate database of signing keys that can be used to update the signature database and revoked signatures database. Microsoft requires a specified key to be included in the KEK database so that in the future Microsoft can add new operating systems to the signature database or add known bad images to the revoked signatures database.
After these databases have been added, and after final firmware validation and testing, the OEM locks the firmware from editing, except for updates that are signed with the correct key or updates by a physically present user who is using firmware menus, and then generates a platform key (PK). The PK can be used to sign updates to the KEK or to turn off Secure Boot.
OEMs should contact their firmware manufacturer for tools and assistance in creating these databases. For more info, see Windows 8.1 Secure Boot Key Creation and Management Guidance.
Boot Sequence
Secure Boot Key Generation Using Hsm Free
Secure Boot and 3rd party signing
UEFI driver signing
UEFI Drivers must be signed by a CA or key in the db as described elsewhere in the document, or have the hash of the driver image included in db. Microsoft will be providing a UEFI driver signing service similar to the WHQL driver signing service using the Microsoft Corporation UEFI CA 2011. Any drivers signed by this will run seamlessly on any PCs that include the Microsoft UEFI CA. It is also possible for an OEM to sign trusted drivers and include the OEM CA in the db, or to include hashes of the drivers in the db. In all cases a UEFI driver (Option ROM) shall not execute if it is not trusted in the db.
Secure Boot Key Generation Using Hsm 10
UEFI 驱动必须由CA或者签名数据库中对应的密钥签名,或者存放驱动镜像的hash值到该数据库中。
the db as described elsewhere in the document 即为签名数据库
Any drivers that are included in the system firmware image do not need to be re-verified. Being part of the overall system image provides sufficient assurance that the driver is trusted on the PC.
Microsoft has this made available to anyone who wants to sign UEFI drivers. This certificate is part of the Windows HCK Secure Boot tests.
Boot loaders
The Microsoft UEFI driver signing certificate can be used for signing other OSs. For example, Fedora’s Linux boot loader will be signed by it.
This solution doesn’t require any more certificates to be added to the key Db. In addition to being cost effective, it can be used for any Linux distribution. This solution would work for any hardware which supports Windows 8.1 so it is useful for a wide range of hardware.
Secure Boot Key Generation Using Hsm Video
The UEFI-CA can be downloaded from here: http://go.microsoft.com/fwlink/p/?LinkID=321194. The following links have more information on Windows HCK UEFI signing and submission: