C Generate Certificate With Private Key
Introduction
This document describes the procedure to generate certificates which have to be uploaded with every fresh installation of AMP Virtual Private Cloud (VPC). With the introduction of AMP Private Cloud 3.X, hostnames and certificate/key pairs are required for all of the following services:
Guidelines: If available, use ICSF to store the private key created in Step 1.Unless you use ICSF to store private keys, any user with READ access to the RACF database, or a user authorized to invoke a RACROUTE REQUEST=EXTRACT request, can obtain the default certificate's private key and any user's encrypted password or password phrase.
- Administration Portal
- Authentication (new in Private Cloud 3.X)
- FireAMP Console
- Disposition Server
- Disposition Server - Extended Protocol
- Disposition Update Service
- Firepower Management Center
Sep 09, 2019 Generate a certificate for each service. Create the certificate for Authentication, Console, Disposition, Disposition-Extended, Update server, Firepower Management Center(FMC) service as per the DNS name entry. You need to repeat below certificate generate process for each service (Authentication, Console etc.) Generate Private key openssl. How can I find the private key for my SSL certificate. If you just got an issued SSL certificate and are having a hard time finding the corresponding private key, this article can help you to find that one and only key for your certificate. Of course the certificate returned by the CA does not contain a private key. But it is stored as.key file on the harddrive. The X509Certificate2 class has a property called PrivateKey which I guess will associate a private key with the certificate, but I can't find a way to set this property. Sep 11, 2018 To generate a public and private key with a certificate signing request (CSR), run the following OpenSSL command. As a security precaution, always generate a new CSR and private key when you are renewing a certificate. Clinging to the same private key is a. Guidelines: If available, use ICSF to store the private key created in Step 1.Unless you use ICSF to store private keys, any user with READ access to the RACF database, or a user authorized to invoke a RACROUTE REQUEST=EXTRACT request, can obtain the default certificate's private key and any user's encrypted password or password phrase.
Here, we will discuss a quick way to generate and upload the required certificates. You may tweak each of the parameters, including the hashing algorithm, key size, and others, as per your organization's policy, and your mechanism of generating these certificates might not match with what is detailed here.
Prerequisites
Components Used
Cisco recommends that you have knowledge of these topics:
- Windows Server 2008 onwards
- AMP Private Cloud installation
- Public Key Infrastructure
Requirements
The information in this document is based on these software and hardware versions:
- Windows Server 2008
- CentOS 7
- AMP Virtual Private Cloud 3.0.2
Warning: The procedure mentioned below can vary as per your CA server configuration. It is expected that the CA server of your choice is already provisioned and the configuration of the same has been completed. The following technote just describes an example of generating the certificates and Cisco TAC will not be involved in troubleshooting issues related to certificate generation and/or CA server issues of any kind.
Generate Certificates on Window Server
Ensure that the following roles are installed and configured on your Windows Server.
- Active Directory Certificate Services
- Certification Authority
- Certification Authority Web Enrollment
- Online Responder
- Certificate Enrollment Web Service
- Certificate Enrollment Policy Web Service
- Active Directory Domain Services
- DNS Servers
- Web Server (IIS)
Generate a Certificate Signing Request (CSR)
Step 1. Navigate to MMC console, and add the Certificates snap-in for your computer account as shown in the image here.
Step 2. Drill down Certificates (Local Computer) > Personal > Certificates.
Step 3. Right click on the empty space and select All Tasks > Advanced Operations > Create Custom Request
Step 4. Click Next at the Enrollment window.
Step 5. Select your certificate enrollment policy and click Next.
Step 6. Choose the template as Web Server and click Next.
Step 7. If your 'Web Server' template has been configured correctly and is available for enrollment, you will see the status as 'Available' here. Click 'Details' to expand click on Properties.
Step 8. At a minimum, add the CN and DNS attributes. The rest of the attributes can be added as per your security requirements.
Step 9. Optionally, give a Friendly Name under the General tab.
Step 10. Click on the PrivateKey tab and ensure that you're enabling Make private key exportable under the Key Options section.
Step 11. Finally, click on OK. This should lead you to the Certificate Enrollment dialog from where you can click on Next.
Step 12. Browse to a location to save the .req file which will be submitted to the CA server for signing.
Submitting the CSR to the CA and generating the certificate
Step 1. Navigate to your MS AD Certificate Services Web Page as below and click 'Request a Certificate'
Step 2. Click on the advanced certificate request link.
Step 3. Click on Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
Step 4. Open the contents of the previously saved .req file (CSR) via Notepad. Copy the contents and paste it here. Ensure that the Certificate Template is selected as Web Server
/download-key-generator-for-any-software.html. Step 5. Finally, click on Submit.
Step 6. At this point, you should be able to Download the certificate as shown in the image here.
Exporting the Private Key and converting to PEM format
Step 1. Install the certificate into your Certificate Store by opening the .cer file and clicking on Install Certificate.
Step 2. Navigate to the MMC snap-in that was selected earlier.
Step 3. Navigate to the store where the certificate was installed.
Step 4. Right click the correct certificate, select All Tasks > Export.
Step 5. At the Certificate Export Wizard, confirm to export the private key as shown in the image.
Step 6. Enter a password and click Next to save the private key on your disk.
Step 7. This will save the private key in .PFX format, however, this needs to be converted to .PEM format to use this with AMP VPC.
Step 8. Install OpenSSL libraries from here:https://wiki.openssl.org/index.php/Binaries
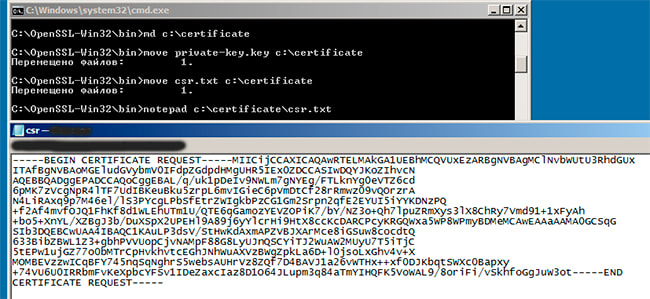
Step 9. Open a command prompt window and change to the directory where you installed OpenSSL.
Step 10. Run the following command to extract the private key and save it to a new file: (If your PFX file is not in the same path as where the OpenSSL library is stored, you will have to specify the exact path along with the filename)
Step 11. Now run the following command to also extract the public cert and save it to a new file:
Generate Certificate on Linux Server
Ensure that the Linux server that you're trying to generate the required certificates has the OpenSSL libraries installed. Verifying if this and the procedure listed below will vary from the Linux distribution that you're running. This portion has been documented, as done on a CentOS 7 server.
Generate Self Signed RootCA
Step 1. Generate the Private Key for Root CA certificate
Step 2. Generate the CA certificate
Generate a certificate for each service
Create the certificate for Authentication, Console, Disposition, Disposition-Extended, Update server, Firepower Management Center(FMC) service as per the DNS name entry. You need to repeat below certificate generate process for each service (Authentication, Console etc.)
Generate Private key
Replace the <example.key> with actual certificate key such as Auth-Cert.key.
Generate CSR
Replace the <example.csr> with actual certificate CSR such as Auth-Cert.csr
Generate Certificate
Replace <example.csr>, <example.crt> with actual certificate CSR and certificate name
Adding The Certificates to AMP VPC
Step 1. Once the certificates are generated from any of the above methods, upload the corresponding certificate for each of the services. If they have been generated correctly, all the check marks are enabled as seen in the image here.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
-->A Key Vault (KV) certificate can be either created or imported into a key vault. When a KV certificate is created the private key is created inside the key vault and never exposed to certificate owner. The following are ways to create a certificate in Key Vault:
Create a self-signed certificate: This will create a public-private key pair and associate it with a certificate. The certificate will be signed by its own key.
Create a new certificate manually: This will create a public-private key pair and generate an X.509 certificate signing request. The signing request can be signed by your registration authority or certification authority. The signed x509 certificate can be merged with the pending key pair to complete the KV certificate in Key Vault. Although this method requires more steps, it does provide you with greater security because the private key is created in and restricted to Key Vault. This is explained in the diagram below.
The following descriptions correspond to the green lettered steps in the preceding diagram.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault returns to your application a Certificate Signing Request (CSR)
- Your application passes the CSR to your chosen CA.
- Your chosen CA responds with an X509 Certificate.
- Your application completes the new certificate creation with a merger of the X509 Certificate from your CA.
- Create a certificate with a known issuer provider: This method requires you to do a one-time task of creating an issuer object. Once an issuer object is created in you key vault, its name can be referenced in the policy of the KV certificate. A request to create such a KV certificate will create a key pair in the vault and communicate with the issuer provider service using the information in the referenced issuer object to get an x509 certificate. The x509 certificate is retrieved from the issuer service and is merged with the key pair to complete the KV certificate creation.
The following descriptions correspond to the green lettered steps in the preceding diagram.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault sends an TLS/SSL Certificate Request to the CA.
- Your application polls, in a loop and wait process, for your Key Vault for certificate completion. The certificate creation is complete when Key Vault receives the CA’s response with x509 certificate.
- The CA responds to Key Vault's TLS/SSL Certificate Request with an TLS/SSL X.509 certificate.
- Your new certificate creation completes with the merger of the TLS/SSL X.509 certificate for the CA.
Asynchronous process
C Generate Certificate With Private Keys
KV certificate creation is an asynchronous process. This operation will create a KV certificate request and return an http status code of 202 (Accepted). The status of the request can be tracked by polling the pending object created by this operation. The full URI of the pending object is returned in the LOCATION header.
When a request to create a KV certificate completes, the status of the pending object will change to “completed” from “inprogress”, and a new version of the KV certificate will be created. This will become the current version.
First creation
When a KV certificate is created for the first time, an addressable key and secret is also created with the same name as that of the certificate. If the name is already in use, then the operation will fail with an http status code of 409 (conflict).The addressable key and secret get their attributes from the KV certificate attributes. The addressable key and secret created this way are marked as managed keys and secrets, whose lifetime is managed by Key Vault. Managed keys and secrets are read-only. Note: If a KV certificate expires or is disabled, the corresponding key and secret will become inoperable.
If this is the first operation to create a KV certificate then a policy is required. A policy can also be supplied with successive create operations to replace the policy resource. If a policy is not supplied, then the policy resource on the service is used to create a next version of KV certificate. Note that while a request to create a next version is in progress, the current KV certificate, and corresponding addressable key and secret, remain unchanged.
Self-issued certificate
To create a self-issued certificate, set the issuer name as 'Self' in the certificate policy as shown in following snippet from certificate policy.
If the issuer name is not specified, then the issuer name is set to 'Unknown'. When issuer is 'Unknown', the certificate owner will have to manually get a x509 certificate from the issuer of his/her choice, then merge the public x509 certificate with the key vault certificate pending object to complete the certificate creation.
Partnered CA Providers
Certificate creation can be completed manually or using a “Self” issuer. Key Vault also partners with certain issuer providers to simplify the creation of certificates. The following types of certificates can be ordered for key vault with these partner issuer providers.
Get Certificate Private Key
| Provider | Certificate type |
|---|---|
| DigiCert | Key Vault offers OV or EV SSL certificates with DigiCert |
| GlobalSign | Key Vault offers OV or EV SSL certificates with GlobalSign |
A certificate issuer is an entity represented in Azure Key Vault (KV) as a CertificateIssuer resource. It is used to provide information about the source of a KV certificate; issuer name, provider, credentials, and other administrative details.
Note that when an order is placed with the issuer provider, it may honor or override the x509 certificate extensions and certificate validity period based on the type of certificate.
Authorization: Requires the certificates/create permission.